IO Reports
IO Reports can now be generated and customized via API -- read more!
IO Reports is a dynamic ecosystem of reports designed to give you a full view of lifestyle and market trends. Featuring two reports — NeighborhoodIntel and Neighborhood Market Report — IO Reports enables you to provide clients and prospects with a comprehensive view of a community’s character and real estate market dynamics.
While IO Reports are available for the NeighborhoodIntel report in the U.S. and Canada, at this time Neighborhood Market Report is only available in the U.S.
These reports are packed with top-tier insights to give you a better understanding of any neighborhood and, in the US, a clear view of local real estate conditions, including real-time data on active listings, median pricing, days on market, and other key metrics.
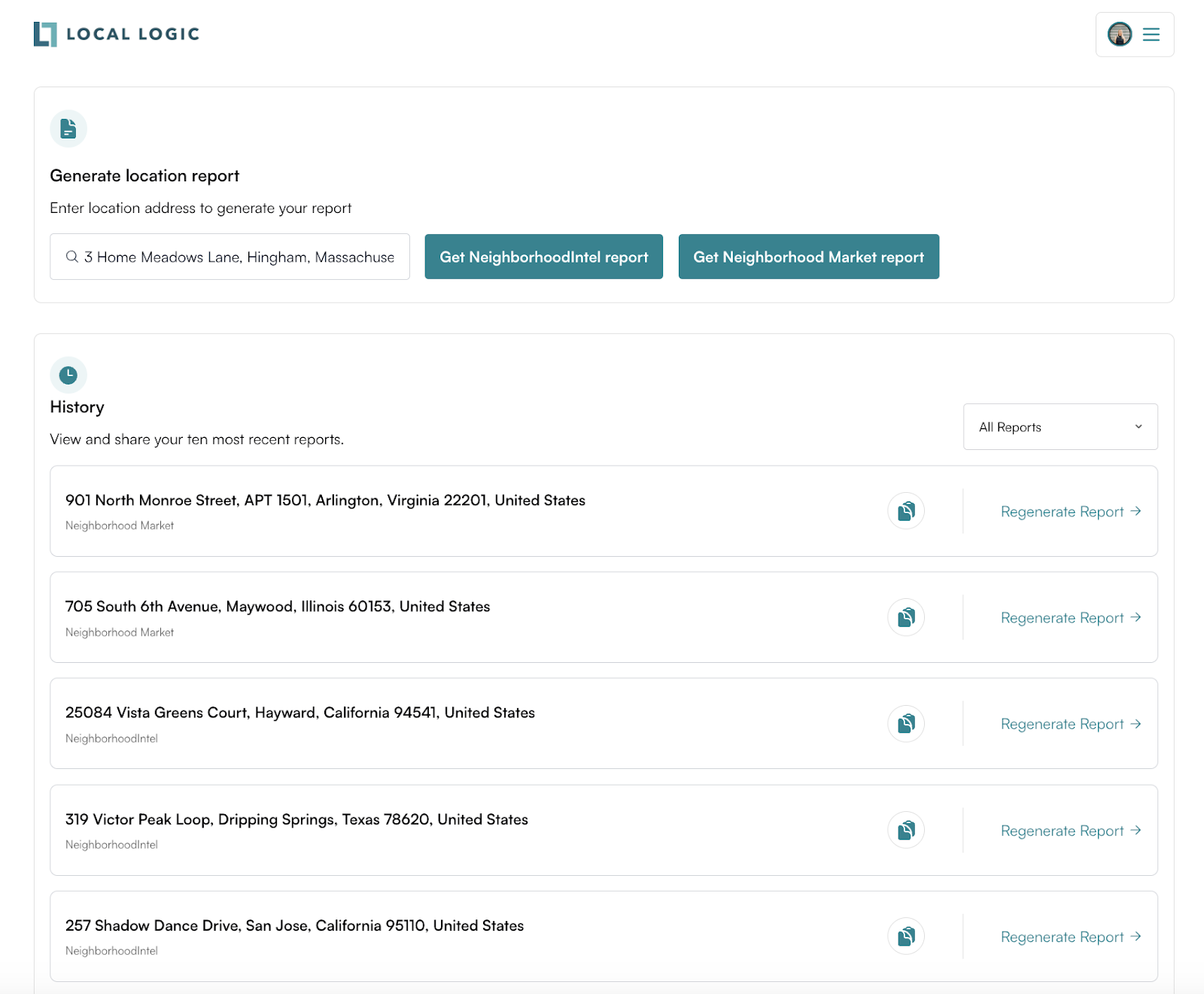
Implementation of IO Reports
IO Reports via API
IO Reports are now supported via API-based implementation! The IO Reports API allows brokerages, MLSs, and real estate platforms to trigger personalized NeighborhoodIntel or Market Trends Reports from any system — without relying on Local Logic's iFrame or redirecting to IO Reports dashboard.
Whether embedded in an existing lead form, email campaign, CRM workflow, or internal dashboard, the API makes it easy to integrate Local Logic’s high-value insights into your user journey.
Single Sign-On (SSO)
IO Reports can be seamlessly integrated with Single Sign-On (SSO), making it easy to provide your agents with secure access to any report. We support both OpenID Connect (OIDC) and Security Assertion Markup Language (SAML) SSO for flexible and secure authentication.
While we support standard OIDC and SAML SSO, we do not support custom SSO authentication flows via JWT.
Security Assertion Markup Language (SAML) SSO
To use SAML, you will need to provide us with your metadata XML file. After receiving this file, we can then agree on an ID for our Service Provider in your system and one for your Identity Provider in ours. Lastly, we will provide you with a Service Provider metadata file that you'll use.
OpenID Connect (OIDC) SSO
To use OIDC, we will need an id, a secret and an issuer URL. If your issuer URL is not the same URL that hosts your well-known configuration, you will need to provide us with endpoints for authorization, jwks, token and user info. For example, https://example.com is the issuer and the well-known configuration is located at https://example.com/.well-known/openid-configuration. You can find an example of the OpenID configuration here.
The Service Provider initiated sign-in flow is the only one supported.
If at login time some errors related to RelayState occur, you may be using the Identity Provider initiated sign-in flow, which is unsupported
In addition to the credentials and endpoints, we will need to map these attributes:
- first name
- last name
- MLS name (if applicable)
- unique user ID (if applicable)
Lastly, you will need a redirect URL for successful signins: https://reports-sso-prod.auth.us-east-1.amazoncognito.com/oauth2/idpresponse.
Iframe
While IO Reports iframe is available in the U.S. and Canada, at this time Neighborhood Market Report is only available in the U.S.
IO Reports has the ability to provide your customers with direct access to reports within your internal dashboard through an iframe integration, available to site license customers. This integration allows agents to seamlessly interact with the IO Reports dashboard without leaving your platform, creating a more efficient and streamlined user experience.
Key Integration Details
- Iframe Embed:
- The iframe renders IO Reports within your existing dashboard or backend system, enabling users to generate and view reports directly in their workflow.
- The iframe can be embedded on a specific page or module within your platform to ensure reports are easily accessible.
- SSO Requirement:
- Single Sign-On (SSO) is required for iframe integration to ensure secure, authenticated access for all users.
- IO Reports supports OpenID Connect (OIDC) and Security Assertion Markup Language (SAML) protocols for SSO authentication.
- Each agent accessing the iframe must be authenticated via SSO to ensure appropriate access permissions.
- Brand Customization:
- The iframe supports branding customization, allowing you to align the report experience with your company’s look and feel.
- Custom branding options include:
- Color themes
- Company logo
Implementation of IO Reports with iframe
JavaScript
<!DOCTYPE html>
<html>
<head>
<title>IO Reports Javascript Example</title>
<meta charset="UTF-8" />
</head>
<body>
<script
async
src="https://neighborhoodintel.locallogic.co/nmr_sdk.js"
onload="loadIOReports()"
></script>
<style>
#io-reports-widget {
height: 100%;
width: 100%;
}
</style>
<div id="io-reports-widget"></div>
<script>
function loadIOReports() {
LLinitNMR(
"#io-reports-widget",
{
provider: "YOURUNIQUEPROVIDERNAMEHERE",
},
);
}
</script>
</body>
</html>